I stare out at the city from my perch on the top floor of my high-tech fortress. The neon lights of Nexus City stretch out as far as the eye can see, a pulsing, vibrant tapestry of sound and color. I can feel the hum of technology all around me, a constant presence that is as much a part of the city as the concrete and steel.

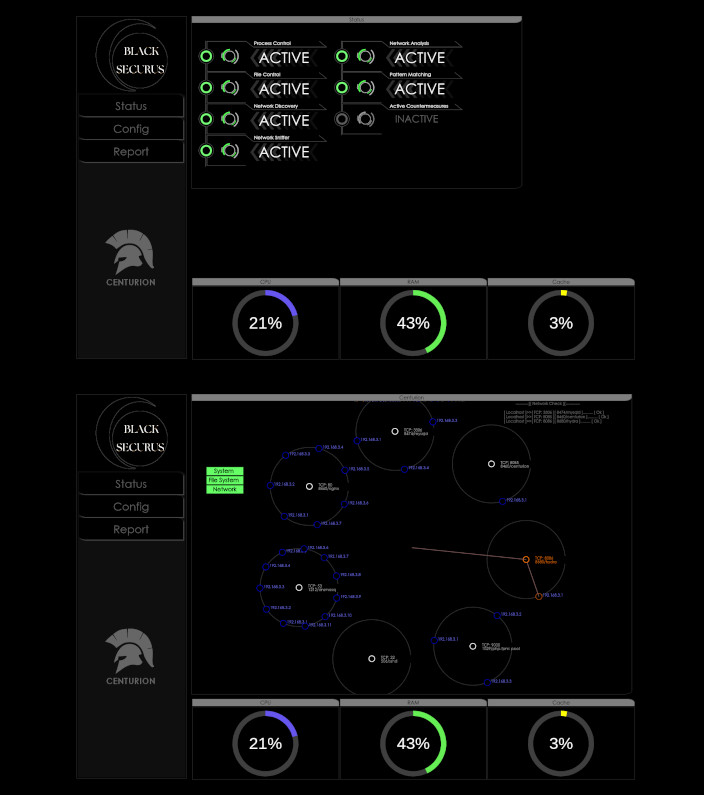
But it’s not just the city that’s high-tech – my home is a testament to the power of technology as well. The walls are lined with screens and holographic displays, displaying everything from the latest news to my personal messages and emails. My cybernetic implants allow me to interface with the systems directly, accessing any information I need with just a thought.
But it’s not all about the gadgets – my home is also a place of comfort and relaxation. The living room is my sanctuary, a place where I can escape the chaos of the city. The soft glow of the artificial fireplace casts a warm, welcoming ambiance, and the plush furniture invites me to sink in and relax.
The virtual reality is my escape hatch, a place where I can leave the real world behind and lose myself in any world I can imagine. Whether I want to explore a fantasy kingdom, visit a distant planet, or just relax on a tropical beach, the virtual reality implant can take me there. It’s a place where I can be anyone I want to be, do anything I want to do.
My home isn’t just about shelter – it’s also about self-sufficiency. I have an indoor hydroponic garden, where I can grow my own food using advanced nutrient solutions and artificial lighting. It’s not easy – the weather in Nexus City can be harsh, and the air quality is often poor – but it’s worth it.

There’s something satisfying about tending to my own crops and knowing that I’m providing for myself. It’s a small reminder that I’m in control of my own destiny, even in a world where so much seems out of my control. The hydroponic garden allows me to control every aspect of the growing process, from the temperature and humidity to the nutrients and lighting. It’s a small piece of paradise in the middle of the city, and I can’t imagine my home without it.