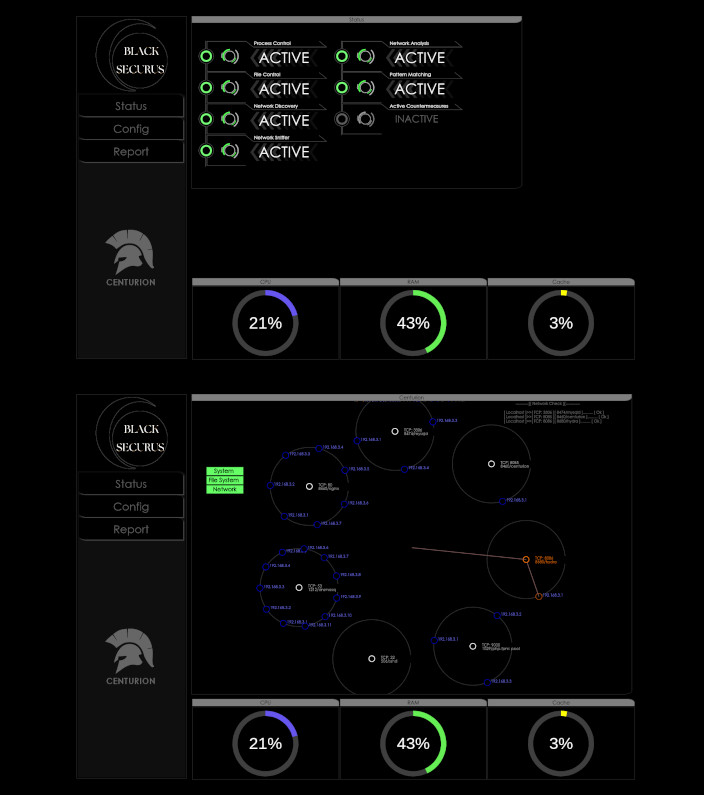
A Security Operation Center (SOC) is a centralized unit that is responsible for monitoring and protecting an organization’s IT systems and infrastructure from cyber threats. It typically consists of a team of security analysts, engineers, and other experts who work together to identify and respond to potential security incidents in real-time. The SOC is responsible for managing an organization’s security tools and processes, analyzing security data and logs, and coordinating incident response efforts. The goal of a SOC is to prevent, detect, and respond to security threats in a timely and effective manner in order to protect an organization’s systems, data, and reputation.
Usual activities in a SOC are:
- Monitoring: The SOC continuously monitors network activity, system logs, and other sources of data to identify potential security threats.
- Analysis: The SOC analyzes data from various sources to determine the nature and severity of any identified threats, and to understand their potential impact on the organization.
- Response: The SOC develops and implements plans to address identified threats, including blocking malicious traffic, isolating compromised systems, and working with other teams to remediate the issue.
- Communication: The SOC coordinates with other teams and stakeholders to communicate the nature and impact of identified threats, and to ensure that appropriate measures are taken to mitigate the risks.
- Documentation: The SOC maintains accurate and comprehensive records of all activities, including threat identification, analysis, and response.
- Continuous improvement: The SOC continually reviews and updates its processes and procedures to ensure that it is effectively identifying and responding to security threats. This may include implementing new technologies and training staff on new techniques and best practices.
- Compliance: The SOC works with other teams to ensure that the organization is compliant with relevant security standards and regulations.
- Education: The SOC may also educate staff and other stakeholders about cybersecurity best practices, including how to identify and report potential threats.